We left off Part 1 setting up our Item lifecycle state names and transitions, the next requirement is to look at the state based security for the item as well as their associated files, something that has become vastly more configurable and flexible with Vault Professional 2015 R2.
The Autodesk Vault Professional legacy item behavior had a simplified security model where Items in working state were editable by any user with Item edit permissions, while all other states (In Review, Released or Obsolete) were locked from user editing, save an administrators ability to delete in certain cases.
Likewise, if desired, administrators could lock the associated or linked files once the item moves out of Work in Progress state. This file locking did have some flexibility with a user access control list managing the linked file access rules, but this could also be considered a limited security model as all locked states were predevined and had this same set of associated file behaviors.
The new Item Lifecycle configuration however allows users to specify access to the item and its linked files on a state by state basis with much greater refinement.
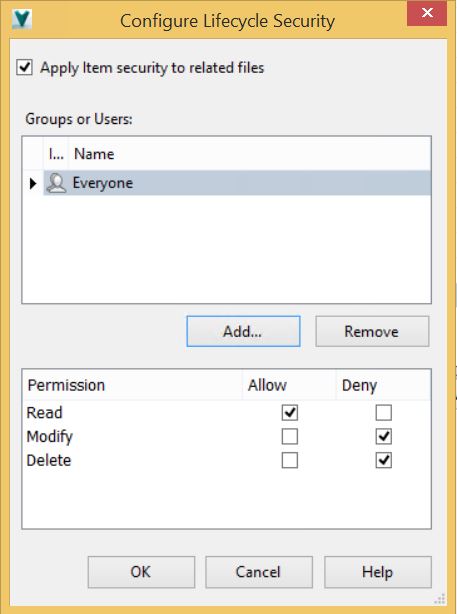
From the lifecycle edit dialog select the appropriate state and from the security tab you can start to configure item access controls. As with the file security settings you will see here that the administrator can add users or groups and set individual access for each. Noting that this access control list is implicit, meaning that as soon as a user or group is permitted or denied access all other users and groups not added to the list will be excluded or denied any access to the item in that state.
There is also an option to remove state based security and simply make the item editable to any users with Item editing permissions, more of a legacy style approach.
As a good practice administrators should retain read only controls on released items and typically any review or obsolete states. These could be augmented with some specific administrator overrides if so desired (delete permissions etc) but its important to keep this logical and maintain lifecycle integrity.
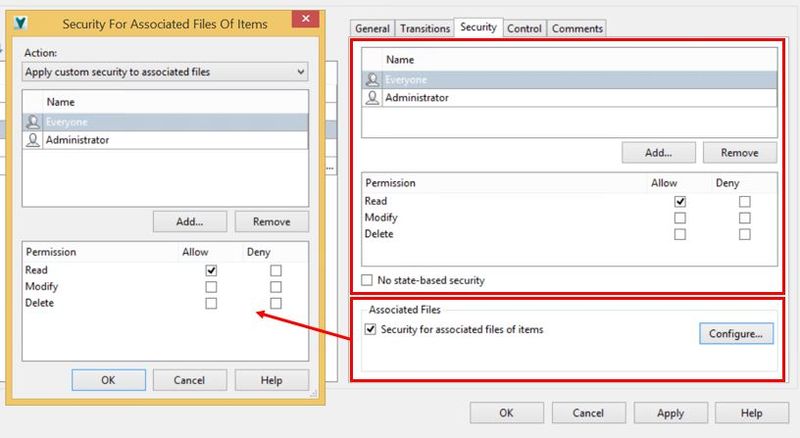
In order to manage user access to the items associated or linked files in each state, select to configure security for associated files. Here the administrator will be able to configure another access control list which manages user access to any file associated with the item in that specific state.
As we have seen in Part 1 of this article it is possible to ensure that associated files are released prior to transitioning an item to a new state, but we do not "synchronise" or mirror the item and file lifecycle states (even if they are assigned to the same lifecycle scheme). So the security we apply here is independent of any other file based security and works as it has in previous releases in that regard. Once again it is worth considering whether your company should use just file based lifecycle security, just item enforced security or build a combination of the two.
By default, the item state is applied to the files (users have same access to the associated files as they do the item), but administrators can choose to set up unique file based access controls (Custom Security) or clear any security overrides in that state (removing file based controls).
By completing these steps for each state we will have a nicely refined set of transition controls, item state based security and associated file controls, meaning the lifecycle configuration is almost complete.
We will stop here though and pick up the last few settings in Part 3 of this blog arch looking at setting the state controls including released or obsolete state identification and purge controls.
-Allan